HIGH RISK SECURITY
Secure
Step-Up Authentication
Increase the Level of Security for Higher-risk Transactions

Smarter, Stronger Authentication for High-Risk Moments
Identity verification shouldn’t end after customer onboarding. Monitoring activity continuously is imperative as customers (or fraudsters) interact and transact with your business. Step-up authentication offers a means to keep customers and your business safe with minimal friction when requiring access to sensitive data.
Trigger secure, step-up authentication using fast ID verification or selfie biometrics—only when additional assurance is needed.
Leverage advanced AI and machine learning to identify fraud and flag bad actors using dynamic watchlists.
Get 100% automated identity verification with clear yes/no outcomes in seconds—no manual review required.
Ensure the user or ID is physically present at the time of re-authentication with built-in liveness detection.
Replace outdated knowledge-based authentication with modern, secure, and user-friendly identity verification.
Three Common Instances to Implement Step-Up Authentication
Monitor large purchases or high-dollar amount transfers from one account to another. These are ideal instances for step-up authentication, especially for higher risk anomaly transactions.
Requests to change contact information or personal information on user accounts, or if a user is logging in from a new location, can require step-up authentication to keep accounts and identities safe.
Trigger ID re-authentication or biometric verification when there are multiple entries of incorrect credentials by the user for secure access.
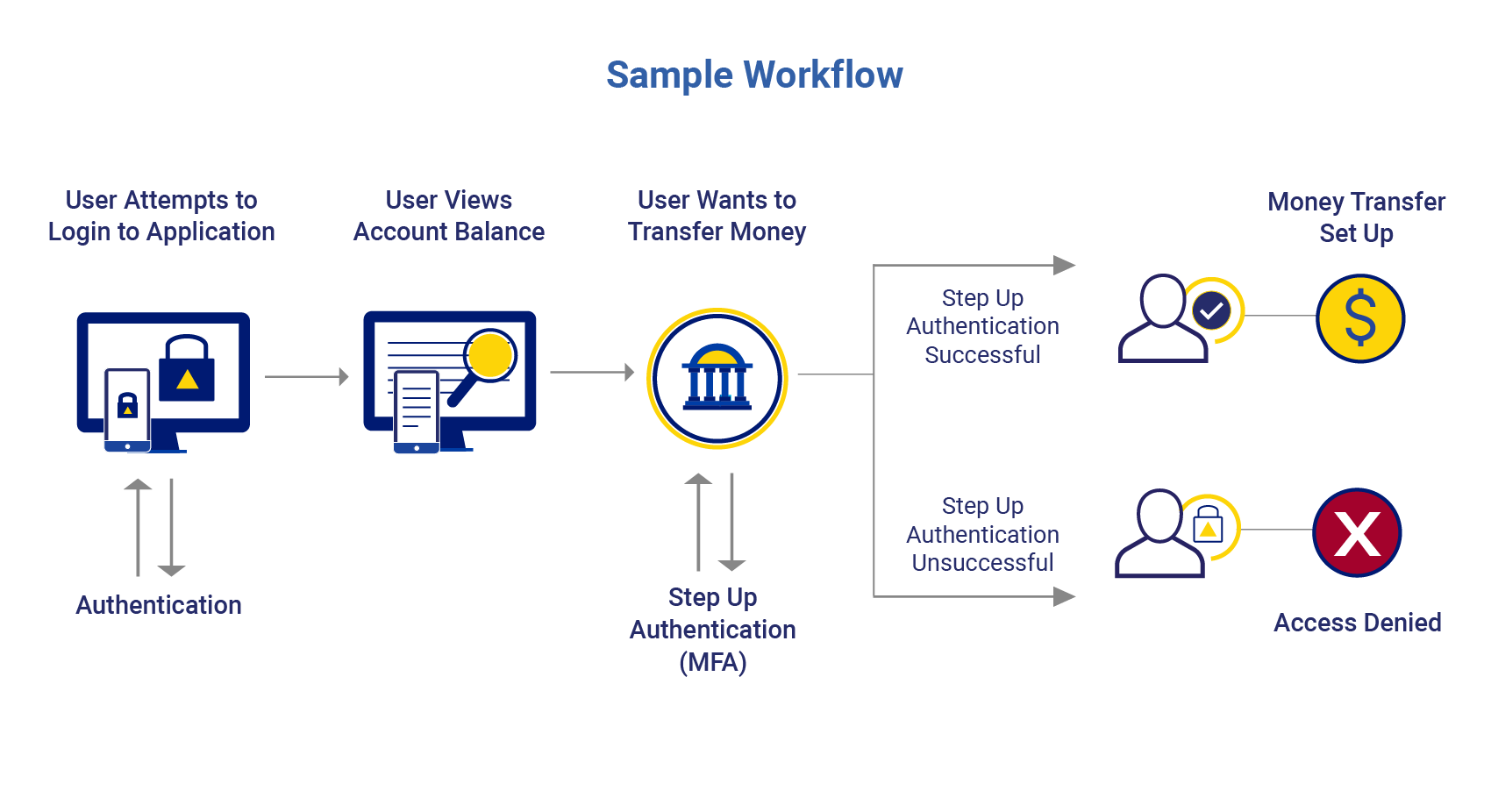
How Step-Up Authentication Works
Not all user actions carry the same level of risk—so why treat them the same? Step-up authentication adds an extra layer of identity verification only when it’s needed, such as during high-value transactions or suspicious activity. The diagram below illustrates how AuthenticID intelligently evaluates risk signals and triggers enhanced authentication at key moments, helping you protect your users without disrupting their experience.
Enhancements for the Most Comprehensive Identity Solution
AuthenticID’s facial biometric technology provides a fast, simple way to authenticate an individual by matching a person’s selfie to the photo on a government-issued ID, profile picture, or any other image of a person’s face with complete accuracy.
See our Identity Verification in Action
Explore the benefits of Identity Proofing. Our Identity Verification technology can be tailored for any industry with custom workflows to meet your use case needs.

FAQs about
Step Up Authentication
READ MORE FAQs Step-up authentication aims to enhance the user experience by implementing additional levels of authentication only when it’s absolutely essential. Unlike standard static multi-factor authentication, which necessitates extra steps for every sign-in or specific action, step-up authentication primarily strengthens security measures in risk based authentications.
Consequently, for most routine actions, users can enjoy a smooth and seamless experience without the need for cumbersome security measures. However, in situations involving more sensitive procedures like modifying personal information or conducting substantial transactions, users can appreciate the heightened level of adaptive authentication, reassuring them that their accounts and data remain secure.
Multi-factor authentication (MFA) is when users are asked to provide multiple forms of authentication to prove their identity when higher levels of assurance are required. Since step-up authentication requires users to produce an additional form of authentication, it thus utilizes MFA and MFA techniques.
Use step-up authentication with multi-factor authentication for additional layers of authentication when users are requesting access to sensitive resources.
There are multiple authentication methods and they are not created equal. Each method carriers a different security level. Additional methods of authentication include MFA, SMS, KBA, Biometrics, Voice, Tokens, Authenticator Apps, Security Keys, etc.
Utilizing facial biometric authentication, otherwise known as a taking a selfie, in combination with liveness detection typically offers a higher level of security. This combination can ensure the person taking the selfie is actually present and stop the most sophisticated spoofing attempts.
AuthenticID’s deepfake detection software is easy to integrate and can be white labeled to fit into any company’s website, app, and/or workflow. AuthenticID offers customizable workflows and plug-and-play APIs and SDKs to connect to workflows with ease.
Let’s Connect
If you have product questions, we have answers.
Our team is here to help.
Schedule My Demo
Discover why AuthenticID leads in identity verification—helping you reduce risk, boost conversions, and cut costs with secure, frictionless identity proofing.