Zero-Knowledge Proofs offer strong assurances of authenticity, integrity, and confidentiality, all while preserving the confidentiality of protected information–which is why they have become so popular in cybersecurity today.
As cybercriminals become more sophisticated with their tactics and traditional username-password methods of Proof of Identity become weaker, the power of Zero-Knowledge Proofs could prove monumental for the industry.
While the definition of Zero-Knowledge Proofs can be elusive, they are actually quite practical when used in real-life scenarios. This article will provide further detail about Zero-Knowledge Proofs, how they work, the benefits they offer, and what they look like in practice.
What Is a Zero-Knowledge Proof?
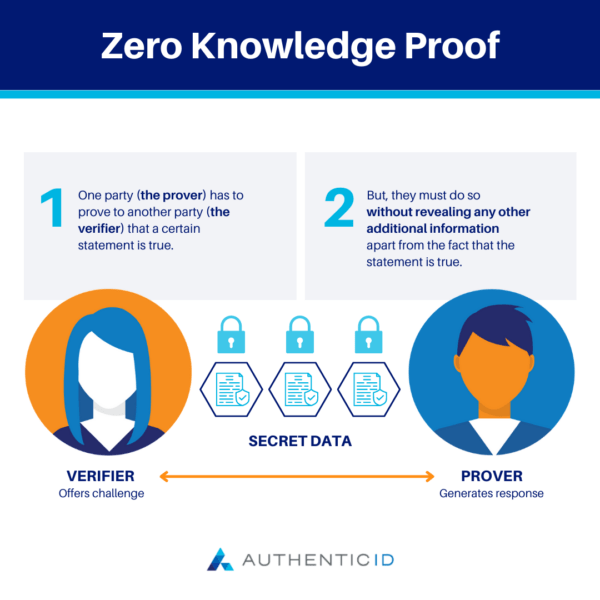
Zero-Knowledge Proof (ZKP) is a cryptographic protocol in the cybersecurity world. With a ZKP, one party (the prover) has to prove to another party (the verifier) that a certain statement is true. But, they must do so without revealing any other additional information apart from the fact that the statement is true.
Put differently, a Zero-Knowledge Proof is a simple demonstration of knowledge or possession of a specific piece of information, but you do not reveal what the content of that information is, or any other context related to the private info. As such, ZKPs offer strong levels of security for confidential information but preserve the privacy of the underlying data.
If someone were to witness a Zero-Knowledge Proof between the two parties, they would not find out what the secret information is, just that the two parties proved that the secret exists among them.
So, the only information that is divulged in a Zero-Knowledge Proof is that the proving person knows the secret, not revealing the actual secret information itself or any other information that could lead back to the secret.
How Does a Zero Knowledge Proof Work?
Zero-Knowledge Proofs are based on specific cryptographic techniques that enable a proving party to convince the verifying party that a statement is true without revealing any additional information.
While the intricacies of how ZKPs work can get convoluted to the untrained professional, here is a brief overview of the components and set-up of a Zero-Knowledge Proof, followed by an illustrative example.
- Set-up: The prover and verifier agree on a common set of parameters and cryptographic guidelines; this includes selecting an agreed-upon encryption algorithm and other necessary tools to complete the ZKP
- Statement/Claim: The proving party establishes the statement that they will provide to the verifier (e.g. “I know the solution to the puzzle” or “I have a valid password”)
- Interaction: The prover and verifier interact on multiple iterations, with the prover attempting to convince the verifier of the truthfulness of their statement on each subsequent interaction
- Proof: The proof comes from the verifier offering a random challenge to the prover that’s related to the secret information, but does not involve revealing the secret information; the challenge is designed in such a way that the prover must possess the secret knowledge to respond correctly, so if the prover generates a correct answer to the challenge, it helps to convince the verifier of their knowledge
- Repeat: If the verifier sees that the prover has generated a correct response, they gain confidence in the prover’s claim without divulging the protected statement; these interactions can continue with new challenges and responses until the prover has successfully convinced the verifier with a high degree of confidence
- Completion: Once the prover has successfully convinced the verifier that they possess the secret knowledge beyond a reasonable doubt, the Zero-Knowledge Proof is complete; the security of the secret information is preserved since it was never disclosed or discussed by the two parties
To illustrate this in a more real-world context, we will use a scenario of a locked door with a combination lock on it. Jess wants to prove to Alex that she knows the secret combination to unlock the door, but doesn’t want to reveal the combination itself to retain its security and integrity.
If the two are using a Zero-Knowledge Proof, Jess could demonstrate her knowledge to Alex by going through a number of interactions with him where he provides related challenges to test the validity of her claim.
Alex is trying to test if Jess has simply gotten lucky with her guess of the combination, has memorized the motions by observing someone else who knows the combination to the lock, or any other scenario where she does not truthfully possess the lock’s combination.
To test this, Alex could manipulate the lock in a new way to see if Jess could continue to unlock it. After performing enough of these challenges successfully, Alex will eventually feel confident that Jess knows the combination, even without her explicitly stating the combination to him out loud. Alex himself may never know the actual combination either, he simply sees Jess continuing to unlock it through subsequent challenges.
Of course, this looks different in an online context. However, the principles remain the same.
Benefits of Zero Knowledge Proofs
In using Zero-Knowledge Proofs, parties can establish trust and verify the validity of claims or statements without exposing secret information.
1. Privacy & Confidentiality:
The primary benefit of ZKPs is the high level of privacy they maintain for sensitive information. By allowing a prover to demonstrate their knowledge without revealing the actual information, the sensitive data is kept confidential.
2. Trust & Confidence:
Zero-Knowledge Proofs enhance trust between parties and can enable efficient verification of statements or claims. Verifiers can be confident in the truthfulness of the prover’s statement, without having to rely on their word alone.
3. Non-Transferable:
Lastly, ZKPs are non-transferable, meaning the proof itself cannot be reused or presented by someone other than the knowledgeable party. Given the series of interactions and the randomness of the challenges presented by the verifier, only provers who actually possess the secret statement will be able to complete the proof. In this way, ZKPs work to prevent unauthorized access to sensitive information.
Common Uses of Zero Knowledge Proofs
As it relates to cybersecurity, Zero-Knowledge Proofs have a number of helpful applications. Here are some of the most common uses of ZKPs in the digital world.
- Authentication protocols: a user can prove their identity or possession of a credential without revealing or sharing sensitive information
- Secure communication: parties can verify that they’re speaking with the appropriate individuals without having to fully disclose their identities
- Anonymous transactions: ZPKs can hide the identity of the sender and recipient, and shield other transaction details while ensuring the validity of the transaction

