Knowledge Based Authentication or KBA for short is a security process that requires asking users for answers to personal information questions to authenticate their identity when accessing accounts or services. Users are required to answer questions that only the individual would know the answer to; for example, secret phrases, names of relatives, or prior transactions. There are three types of KBA:
- Static KBA, in which the question is chosen by the user upon account creation
- Dynamic KBA, in which questions are generated in real-time, with more specific questions gathered from credit reports, marketing databases, etc.
- Enhanced KBA uses both static and dynamic questions, as well as other methods, including biometrics like fingerprints or facial recognition technology.
What Is Knowledge-Based Authentication?
Privacy concerns and increasing cyberattacks have given rise to numerous solutions meant to prevent or reduce identity-driven fraud. One of these solutions is a strategy called knowledge-based authentication (KBA).
Knowledge-based authentication is an identity verification process in which a user is asked a series of questions that demonstrate they possess personal (and presumably private) information. For example, an individual might have to answer pre-selected questions about their family history when attempting to log into their bank account from a new device.
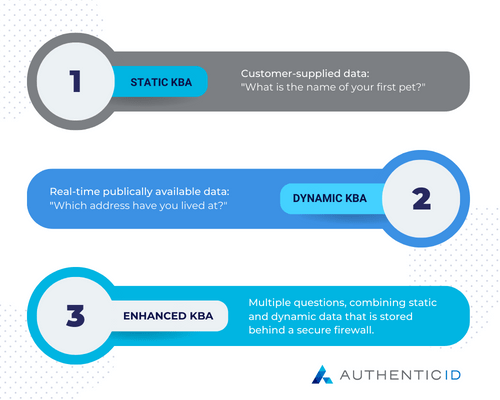
KBA questions fall into one of three broad categories, which are as follows:
What is Static KBA?
Static KBA questions are chosen by consumers when they set up their accounts. Typically, a user will have to select between one to five questions and provide standardized answers for each one. If future activity triggers a network’s KBA protocol, the user must answer one or more of these questions to access their account.
A common example of a KBA question is, “What was the name of your best friend in high school?”
What is Dynamic KBA?
Dynamic KBA questions are unique in that they are generated in real-time. These questions require users to provide information that the platform has gathered from marketing databases, public records databases, etc. For instance, a dynamic KBA question may list four separate addresses and ask the user to select which address they have previously been associated with.
What is Enhanced KBA?
Enhanced knowledge-based authentication is the most robust KBA method. This approach uses a combination of dynamic and static questions, that is stored behind a firewall.
How Does KBA Work and When Is It Used?
Knowledge-based authentication software is commonly used by lenders, financial institutions, and other entities that manage consumers’ assets or store confidential data. Internet service providers, cable companies, and social media organizations may also use KBA to protect users’ accounts and guard against fraud.
Typically, KBA questions are only asked if the user meets one or more criteria that raise concerns about their identity, such as logging into an account from an unrecognized device or network. They’re not typically used to authenticate every login unless the organization chooses to enforce them universally.
Consumers can also force their browsers to prompt for questions every time by blocking cookie data and declining to use “remember me” functions on websites.

How Effective is KBA?
Knowledge-based authentication always takes the form of one or more questions that require users to provide information.
Generally, static KBA questions ask for information that has never been a part of any public record. A few examples include the name of the user’s first pet, their best friend’s last name, or their favorite food. The downside with static KBA is that many sites ask identical or similar questions, which means that users provide identical answers. If their information is compromised on one site, bad actors might be able to circumvent static KBA protections on other platforms as well.
On the other hand, dynamic KBA questions contain information retrieved from a user’s public records or existing marketing databases. This information is generally well protected. However, since the information is documented on one or more digital records, it is accessible should a hacker gain access to a server where this information is stored.
Advantages and Disadvantages of KBA
The main advantage of KBA is that it provides a second layer of verification for added security. Each variation of KBA comes with pluses and minuses. With static KBA questions answers are typically not documented. For example, if someone stole your wallet, they wouldn’t have access to private memories like the name of your beloved first pet or go-to midnight snack.
Dynamic KBA questions are generated using public records and marketing data, which fraudsters could hypothetically get their hands on. Fortunately, many dynamic KBA systems generate questions randomly and require users to provide answers within a few minutes or get locked out.
You might feel confident in KBA’s ability to protect you from fraud, but while it can certainly hinder fraudsters, it is by no means foolproof.
Remember, static KBA questions are pretty common. As a result, your answers to these questions are probably accessible through multiple websites. Although a hacker might not be able to sneak past your bank’s firewall, they may be able to obtain your answers from a less protected site that also uses KBA technology, or through social media accounts. That is why it’s always good advice not to overshare on social.
Dynamic KBA isn’t unbeatable either. Skilled hackers can rapidly scour the internet to find public records data that they can use to successfully answer personal questions about your past. This has become even easier thanks to public records platforms that compile data from multiple local, state, and national databases.
What New Technologies Are Poised to Replace KBA?
The rise of machine learning and artificial intelligence tools have provided businesses with a viable replacement for KBA technology. For example, consider liveness detection technology, which uses computer vision to discern between fake and real live faces when authenticating users with facial biometrics.
Continuous liveness detection is particularly effective when paired with technologies like behavioral biometrics, which analyzes a user’s previous behavior to determine how their current activities align with documented habits.
Cumulatively, these solutions will not only replace KBA, but they will also provide users with better protection against fraud.

