Injection attacks pose significant security risks to applications, websites, and other systems. Though they were originally discovered in the late 1990s, decades later, cybercriminals continue to execute injection attacks as a way to exfiltrate data, compromise or modify databases, and engage in other exploitative activities for their personal gain.
What Is an Injection Attack?
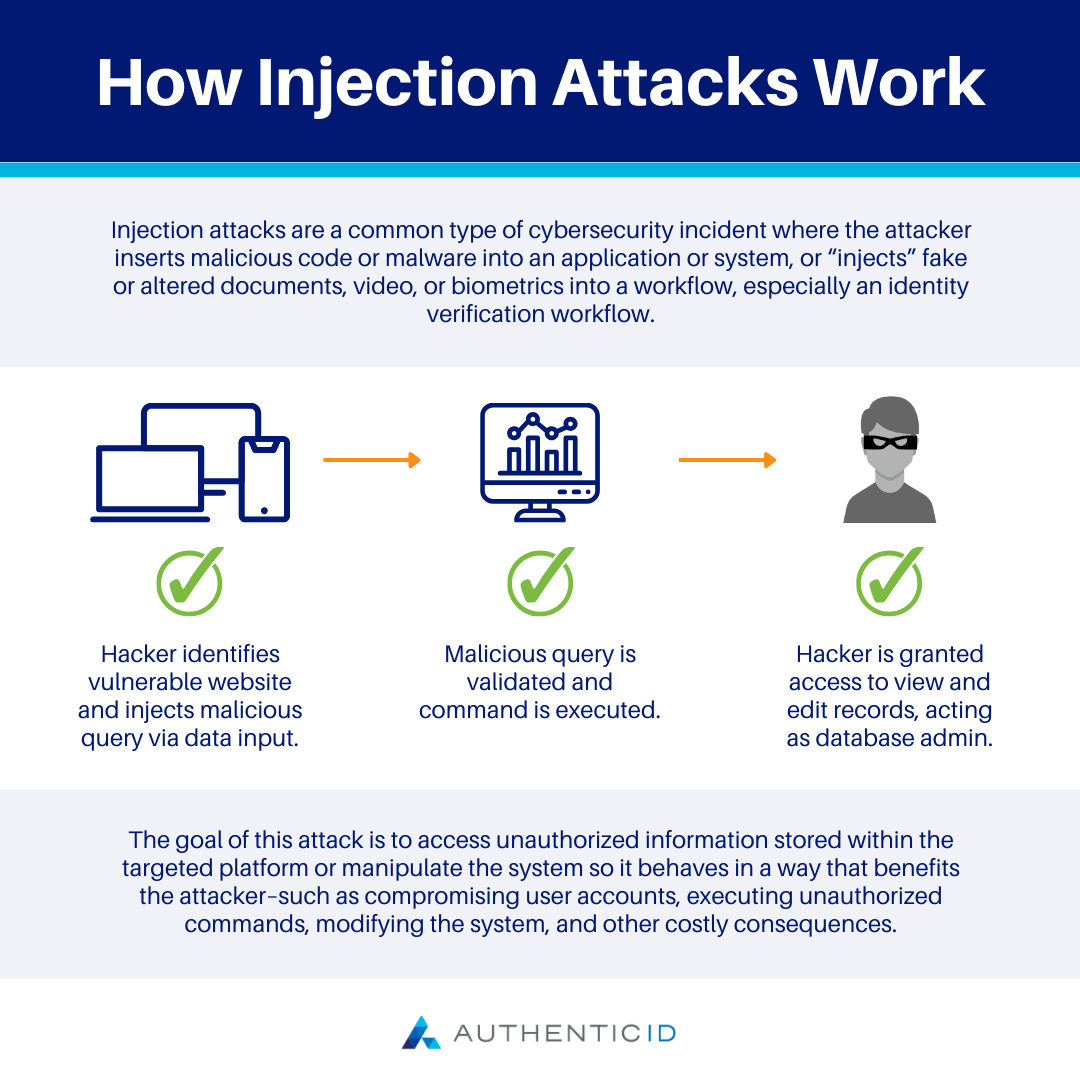
Injection attacks are a common type of cybersecurity incident where the attacker inserts malicious code or malware into an application or system, or “injects” fake or altered documents, video, or biometrics into a workflow, especially an identity verification workflow.
The goal of this attack is to access unauthorized information stored within the targeted platform or manipulate the system so it behaves in a way that benefits the attacker–such as compromising user accounts, executing unauthorized commands, modifying the system, and other costly consequences.
How Does an Injection Attack Occur?
Code Injection Attack
Injection attacks are typically completed by injecting corrupt code into input fields or parameters, causing the system to interpret it as a command or query and alter how the program operates. The attacker seeks out vulnerabilities within the program to enable this type of attack, specifically related to its input validation mechanism–or lack thereof.
When implemented correctly, input validation should allow external parties to only input properly formatted data into a system. Otherwise, as with injection attacks, improper data can interrupt the normal functionality of the application.
Commonly, injection attacks are executed using special input data such as SQL commands, scripts, or operating system commands. These are injected into the system’s input fields, parameters, or data streams, where the application processes them as if they were legitimate commands or queries.
For instance, an attacker might use a SELECT statement to retrieve certain data from the system that they are not authorized to access, or a DELETE statement to eliminate records within a database. The specific command or script the attacker uses will depend on their motive for the attack.
Digital Injection Attack
In other cases, a digital injection attack can occur when false data is injected into a workflow of an organizational identity verification platform via the use of cameras, emulators, or other techniques to bypass a device’s input (camera, microphone, fingerprint, etc.) or inject false location or other data to convince the system the data is legitimate. This data could include fake documents, replacing legitimate device camera with deepfake video, or hacking web browsers to send fake data or documents.
This type of injection attack can be difficult for a system to detect as it exploits security gaps in many identity verification systems.
Types of Injection Attacks
Injection attacks refer to a broad type of attack vector, of which there are many possible variations depending on the attacker’s objective.
- Deepfake Video Injection: By using deepfake videos, bad actors can inject those deepfakes into an authentication workflow to mimic a legitimate customer or user any bypass a facial recognition system.
- Voice Authentication Bypass/Injection: New, AI-based voice synthesis technology can allow fraudsters to spoof and synthesize someone’s voice and voice patterns, allowing them to easily bypass voice-activated authentication systems.
- Biometric-based Injection: From the use of artificial fingerprints to even forging vein patterns, these convincing fakes can bypass many authentication platforms.
- SQL Injection: One of the most common types of injection attacks, where attackers place malicious SQL code into input fields or parameters to manipulate an application’s database. Their goal is typically to alter the database, access sensitive data stored within it, or make it inaccessible to verified users.
- Cross-Site Scripting: Attackers may inject malicious scripts, most commonly JavaScript, into web pages that other users will view. These scripts will be executed in the victim’s browser, enabling the attacker to steal session tokens, cookies, or other sensitive data. The attacker may also use this type of injection attack to engage in behaviors on behalf of the victim, further shielding the identity of the perpetrator.
- Command Injection: This occurs when an attacker injects malicious commands into input fields or parameters of an application, allowing them to interact with the operating system. By executing arbitrary commands, they may be able to compromise the system or gain unauthorized access to stored data.
- LDAP Injection: These attacks exploit systems that use LDAP to retrieve data or authenticate users. Malicious LDAP queries can be used by attackers to bypass authentication challenges, access sensitive information, and engage in unauthorized behaviors.
- XML Injection: A type of attack targeting systems that process XML data without a proper input validation method. The perpetrator will inject malicious XML language to disclose certain information, deny service of the application, or otherwise compromise the system.
- Header Injection: Attackers will inject malicious content into HTTP headers to alter the behavior of web servers or applications. This might be used to engage in session fixation or cross-site scripting to execute other types of cyberattacks.
Risks of Injection Attacks
Injection attacks are widespread and can cause devastating outcomes for the compromised system or application. Here are some of the largest risks of injection attacks:
- Data Breaches: An injection attack may enable unauthorized access to sensitive data stored within a system or application, potentially exposing user credentials, personal information, financial data, and more.
- Data Loss: Certain injection attacks aim to manipulate, modify, or delete data stored in an application or database, which can lead to a loss of data integrity for the organization and impact regular operations and user satisfaction.
- Denial of Service: Injection attacks can compromise the regular functioning of an application or system by overwhelming servers or applications with malicious or excessive requests. The result may be costly downtime and inaccessibility of the platform for legitimate users, which can create further consequences.
- Account Takeover: Attackers may gain unauthorized access to user or administrative accounts, which can allow for data breaches, fraudulent transactions, or other behaviors, seemingly completed by a legitimate user.
- Reputational Damage: Organizations that fall victim to injection attacks can experience an erosion of user trust and confidence, which can ultimately tarnish their reputation in the industry.
- Regulatory Consequences: In certain cases, injection attacks may result in non-compliance with industry regulations or data protection laws, which could evoke fines, penalties, or other legal consequences.
Injection Attack Prevention Tips
Because injection attacks can be so varied and target different areas of an application or system, it can be difficult to spot when an attack is underway. However, early detection and prevention are essential to minimizing the risks and potential loss from the attack.
First, implement a robust input validation mechanism to filter out malicious user inputs before they can be interpreted by the system or application. Another important line of defense is to use prepared statements with parameterized queries, preventing attackers from being able to alter query intent for their own objectives.
Regularly monitor logs to spot abnormal behaviors or unusual queries and requests that could hint at an attempted injection attack. You may even consider implementing an anomaly detection system to continually look out for unusual activities and flag them for manual review.
Ensuring legitimate data is entered into a system is crucial. Your identity verification platform should be armed with the latest technology to detect spoofs and deep fakes as these attacks continue to rise.
With robust security controls and proactive risk mitigation strategies, organizations can combat injection attacks and prevent the vulnerabilities that make these devastating incidents possible.

