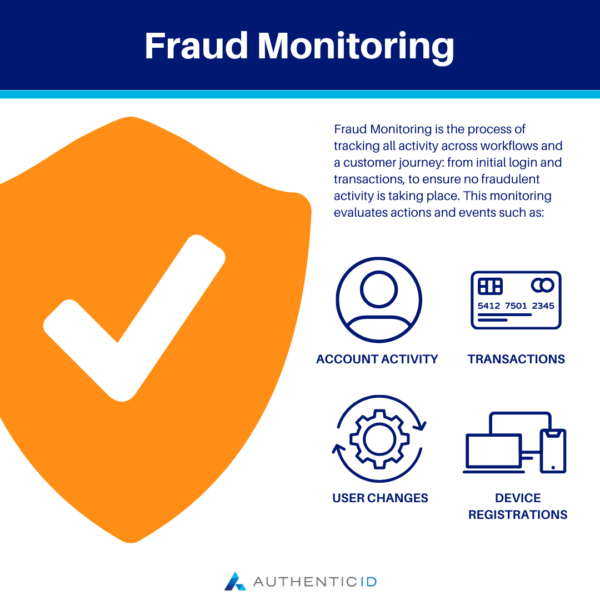
Fraud Monitoring is the process of tracking all activity across workflows and a customer journey: from initial login and transactions, to ensure no fraudulent activity is taking place. This monitoring evaluates actions and events, including account changes, user changes, transactions, and device registrations. Typically, a fraud monitoring system will flag suspicious activity or anomalies in user behavior to stop fraudulent activity and reduce or stop the loss of money, operational expense, as well as damage to brand reputation.
What is Fraud Monitoring?
A modern fraud prevention strategy is built around fraud monitoring. Continuous fraud monitoring involves checking all account activity, not just the first login and subsequent transactions like payments and money transfers. Whether financial or non-financial, all acts and occurrences are examined as part of continuous fraud surveillance. This process covers things like updating the profile of an account owner, adding a beneficiary or payee, and registering devices.
An anti-fraud system must continuously evaluate enormous amounts of data, events, and their context when keeping an eye out for suspicious conduct in order to identify irregularities in user behavior patterns. It’s a strategy that enables financial institutions to react to threats in real-time and thwart fraud.
Using fraud monitoring can allow organizations and businesses to protect themselves from new, emerging forms of fraud while still protecting the customer experience, as well as ensuring a business can meet all regulatory compliances.
Fraud Monitoring and Continuous Transaction Monitoring
Continuous transaction monitoring will use analytical resources to look at all user actions monetary and non-monetary, sensitive and non-sensitive. It monitors all the steps of the login process to the transactions.
The anti-fraud system examines events and actions including adding a new beneficiary or payee, registering a new device, and changing personal information like an account owner’s profile as part of this ongoing monitoring.
The system for preventing fraud examines information about the endeavor and its success or failure. This creates a historical profile for every customer activity prior to, during, and following the action. By creating this thorough historical profile, the system is better able to spot anomalies, which are actions that are not consistent with the account owner’s regular banking actions.
There are various examples of transactional data, some of which include the following:
- Device IP address
- Age of Account
- Geolocation
- Purchase history
- Transaction amount
Fraud Monitoring and Continuous Session Monitoring Compared
Continuous session monitoring is similar, but it simply monitors the banking session. In order to detect, for instance, whether there is a sign that the session is being hijacked by an attacker, continuous session monitoring analyzes all events that occur throughout a banking session and tracks how the behavior of the user or the device has changed inside the session (i.e., session hijacking).
To spot potential threats, continuous session monitoring is carried out across channels and devices. For instance, if a mobile device was used for authentication but the banking session began on a PC. Alternatively, the bank can assist in preventing fraud by requiring authentication using the device that was used to start the session if the user starts a payment from one country and authenticates it in another.
Risk-based fraud detection compares each transaction to statistical models and assigns a risk score to the transaction. Based on information gathered from the session, user, device, and other sources, these ratings are numerical numbers that represent the risk associated with a transaction. Depending on their risk tolerance and corporate policy, organizations can set up separate transaction flows for transactions that cross specific risk thresholds.
To do this, data sets may contain hundreds of different indicators of fraud activity. It also includes cyber-intelligence and takedown services to identify and stop fraudsters operating outside of perimeter defenses and attacking the organization’s clients.