It may seem like a constant theme that instances of fraud and cybersecurity incidents are escalating this year, but this is an ongoing trend that shows no signs of abating. As our world becomes increasingly digital, cybercriminals are quick to exploit new vulnerabilities, posing a significant threat to both consumers and businesses.
In this guide, we’ll examine the different types of fraudsters and emerging tactics and threats to be aware of so you can stay safe and protect your data online.
It may seem like a constant theme that instances of fraud and cybersecurity incidents are escalating this year, but this is an ongoing trend that shows no signs of abating. As our world becomes increasingly digital, cybercriminals are quick to exploit new vulnerabilities, posing a significant threat to both consumers and businesses.
In this guide, we’ll examine the different types of fraudsters and emerging tactics and threats to be aware of so you can stay safe and protect your data online.
Who Is Behind Cybercrime?
The chilling reality is that, in our modern era, anyone at any time can become a victim of a crime orchestrated by an unseen perpetrator on the other side of the globe.
The anonymous nature of these attacks can cause us to forget that an actual individual–or group of individuals—is behind each of these crimes.
Organized Crime Networks
In 2024, it’s becoming more likely that there’s more than one person behind a cyber attack, such as an underground crime ring or consortium of professional hackers who work together to steal, share, and sell your data on the dark web.
Organized cybercrime is big business. If it weren’t, it wouldn’t be so prevalent.
According to some estimates, cybercrime is expected to cost the world a staggering $10.5 trillion annually by 2025, up from $3 trillion in 2015. Thus, cybercriminals have a clear incentive to collaborate and leverage the latest tricks, talents, and tactics to try to gain their share of this illicit wealth.
In recent years, a few organized crime groups have taken the spotlight with a series of high-profile attacks against major organizations, including:
- Scattered Spider: Active since 2022, this is a Russian group of hackers who use tactics like social engineering, phishing, SIM swapping, and MFA fatigue to target the identity credentials of organizations such as Okta, MGM Casino, and Caesars Entertainment. The group is also referred to as Star Fraud, Scatter Swine, Muddled Libra, UNC3944, and other names.
- GambleForce: An Asian-Pacific group that exploits the content management systems (CMS) of various industries to steal credentials, including government, gambling, retail, and more. They typically use SQL injection attacks and open-source tools to bypass authentication checks.
- Charming Kitten APT: An Iranian hacking group that targets defense, military, and other governmental agencies with tactics like malware, phishing, and social engineering. This group is also called APT 35, Newscaster, Phosphorous, Ajax Security Team, and other names.
- FIN8: A financially motivated group active since 2016 that deploys ransomware through a backdoor, though their tactics continue to evolve. They primarily target organizations in entertainment, retail, and hospitality.
Solo Bad Actors
Plenty of sole operators and identity thieves work alone, not as part of a larger group.
These bad actors come from all different ilk and backgrounds and engage in identity fraud as a means to make a living for themselves–either full-time or as a sort of illicit “side hustle.” They might be amateurs or professionals, but either way, they can have a disastrous impact on their identity theft victims.
What Drives Fraudsters?
To understand why someone might be motivated to engage in fraudulent activity and cause such devastation to their victims, you must learn about the “fraud triangle.”
The fraud triangle refers to the three main factors motivating a person to commit fraud.
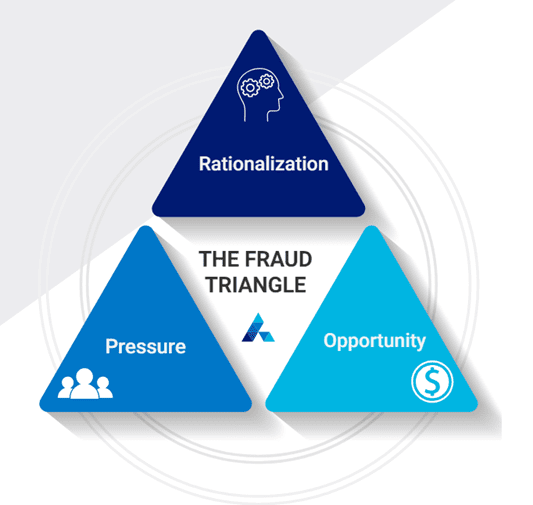
The idea is that when these three elements are present, a person has a motivation for the criminal activity, as they have rationalized it to some degree, they’re facing some kind of pressure, and there is an available opportunity they can seize.
Digital fraud is often easier for opportunists to rationalize, as it’s a faceless and nameless crime in which they are detached from the victim and the potential negative outcome.
Plus, as we’ve discussed above, cybercrime offers a sizable wealth opportunity, and the growing web of organized crime networks is making it more accessible for individuals to get involved in these illegal activities when facing the right pressures.
Emerging Fraudster Tactics in 2024
Each year, consumers and businesses must grapple with the growing threat of fraud and proactively adapt to the new tactics and methods opportunists use to initiate these attacks.
Especially as organized crime groups become more involved in these incidents, their tactics will only become more sophisticated and harder to detect.
Below, we’ll reveal some of the new techniques and methods of individual fraudsters and organized crime syndicates in 2024.
Phishing Kits
Traditionally, phishing attacks require fraudsters to create extremely accurate replicas of a business or organization’s website in the hopes of tricking users into disclosing sensitive information such as their login credentials, payment details, and other data.
Now, cybercriminals are selling phishing kits, or phishkits, which are packages of resources and tools to streamline phishing attacks. These kits allow opportunists with minimal experience and expertise to launch large-scale phishing attacks quickly and effectively.
Fraud-as-a-Service (FaaS)
One discouraging trend is the emergence of fraud-as-a-service (FaaS), which is a business model where professional fraudsters engage in fraudulent activity on behalf of customers in exchange for a fee.
Fraudsters might sell their services, tools, or expertise to customers who want to benefit from fraud but don’t necessarily want to engage in the activities directly. The growth of this model is troubling and puts countless businesses and individuals at risk of an attack. It’s likely that a growing number of people will find it easier to rationalize this activity since they are one step removed from the actual fraudulent behavior.
AI-Generated Fake IDs
AI-powered tools and platforms have quickly taken over all corners of life in the past year, so it’s no surprise that fraudsters are leveraging this advanced technology in their tactics.
Notably, there has been an emerging market of AI-generated fake ID services. Some of these services promise customers hyperrealistic photos of fake identification documents just a few hours after purchase, which they can use to bypass identity verification checks when opening new accounts or support other illegal activities.
Learn More About the State of Identity Fraud in 2025
Check out our 2025 State of Identity Fraud report for a more in-depth look at the emerging threats and trends in the global identity fraud landscape.
